
Cyberattacks
Learn more about cyberattacks on embedded systems

Either to collect information, to alter the functioning of an embedded system, or simply to neutralize it, there are many methods of cyberattacks. They can be classified into two categories, the passive or observational methods of attack and the active methods of attack that require interaction with the equipment.
What is a passive attack ?
Passive attack methods on embedded systems consist in the analysis of the equipment behaviour. They are intended to recover sensitive information, such as encryption keys, certificates, passwords, …
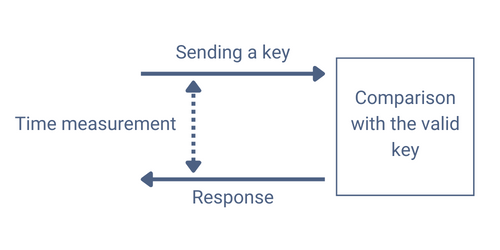
There are also side channel attacks, which exploit vulnerabilities in the implementation of a system. For instance, it is possible to collect information by analysing the evolution of the current consumption of a system or its electromagnetic radiation. An increased power consumption indicates more calculations. Timing attacks allow to know the execution time of some operations, which can be particularly efficient if the algorithm uses a loop to compare keys.
Probing attacks consist in positioning probes on the board to analyse the communication buses between the components, on the factory or maintenance interfaces or directly on the test points of the board.
What is an active attack?
An active attack on embedded systems can be of several natures. If it concerns equipment with an IP interface, it can be a DoS attack (denial of service attack) which aims to make the system unavailable. This can be done for example by flooding the network or by disturbing the connections between devices.
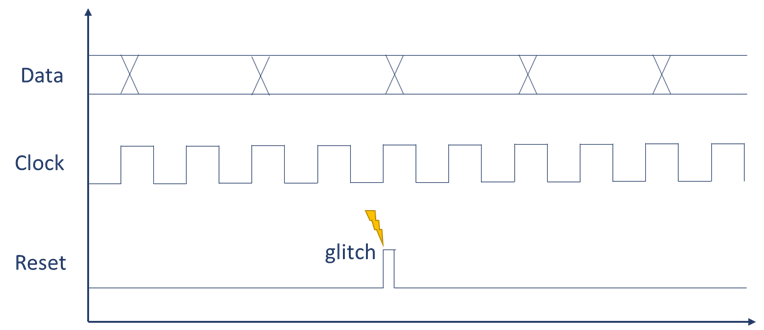
If the hacker has access to the electronic board, he can extract the data contained in the external memories or alter its content. It is also possible to inject faults or glitches on the communication buses to alter the functioning of the system.
What about the security of IFOTEC’s IP equipment ?
Concerning IFOTEC’s secure Ethernet Switches, the security of these fiber optic transmission equipments is taken into account from the design stage.
This is accomplished through the choice:
- Components allowing advanced cryptography functionalities
- A software development using only reliable encryption algorithms
- No access to sensitive data
Furthermore, the integrity of the application is verified at each startup and updates can only be made with firmware authenticated by ourselves.


